OPTIGA™ TPM SLM 9670
Standardized and certified TPM 2.0 security solution for industrial & demanding applications

The OPTIGA™ TPM SLM 9670 is a member of the OPTIGA™ TPM family. It addresses the requirements of industrial and other demanding applications where an extended temperature range, an extended lifetime and industrial-grade quality are key.
Pushing beyond the qualifications processes performed for standard TPMs, the OPTIGA™ TPM SLM 9670 is qualified according to the industrial JEDEC JESD47 standard to enable the requisite performance under demanding environmental conditions.
OPTIGA™ TPM SLM 9670 offers high levels of flexibility to address innovative use cases of Smart Factories and Industry 4.0 that call for robust security:
- Strong digital device ID and device authentication
- Secured communication for data confidentiality and IP protection
- Integrity protection of devices and software incl. software updates
The answer to smart factories`security challenges: OPTIGA™ TPM SLM 9670
OPTIGA™ TPM SLM 9670 offers high levels of flexibility to support innovative smart factory and Industry 4.0 use cases that call for robust security based on:
- Strong digital device IDs and device authentication
- Secured communication for data confidentiality and IP protection
- Integrity protection of devices and software , software updates included
SLM 9670 is equipped with a variety of functions to secure industrial devices and systems. These include:
- Key storage and management
- Identification and authentication
- Signature generation and verification
- Software and firmware integrity attestation
- Secured logging and secured time
OPTIGA™ TPM SLM 9670 is fully compliant with the Trusted Platform Module (TPM) standards issued by the Trusted Computing Group (TCG). It is listed within the TCG Certified Products List based on functional and security evaluations performed by an independent third party according to Common Criteria EAL4+. In addition, it is compliant with FIPS 140-2 Level 2 (Physical Security Level 3).
Based on the open, vendor-neutral global TPM standard created by TCG, the OPTIGA™ TPM family is a widely used and proven solution supported by a far-reaching ecosystem. Major rich operating systems support OPTIGA™ TPM, offering plug-and-play usability. Additionally, a wide selection of software offerings, including libraries and applications, is available from open source projects and leading commercial vendors – also through the Infineon Security Partner Network (ISPN).
- Standardized security chip compliant with TCG TPM 2.0 standard
- Secured storage for critical data and secrets
- Advanced protection mechanisms against physical and logical attacks
- Support of cryptographic algorithms RSA-1028, RSA-2048, ECC NIST P256, ECC BN256, SHA-1, SHA-256
- temp. range -40°C to 105°C
- lifetime of 20 years
- JEDEC JESD47 industrial qualification
- Independently security evaluated and certified
- Industrial PCs
- Servers
- Programmable Logic Controllers (PLC)
- Industrial Network Infrastructure & Equipment Including
- Gateways
- Routers
- Wireless Access Points
- Switches

Related links
GitHub
Functional blocks of a TPM
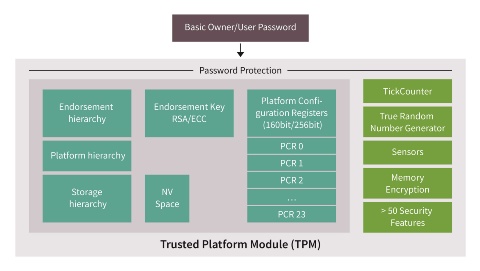
The TPM supports key and lifecycle management with its unique endorsement key and key hierarchies. The non-volatile memory can be used to securely store sensitive data like certificates. It is based on tamper-resistant hardware with more than 50 security features including sensors and memory encryption capabilities for hardened protection of secrets. The TPM also features a secure tick counter for a trusted time source.
Block diagram of a TPM secured microcontroller
Ecosystem and ISPN partner support of OPTIGA™ TPM

With more than 15 years of experience in designing TPM-based solutions and more than 20 scientific publications, the Fraunhofer Institute for Secure Information Technology (SIT) is one of the leading experts in the field of Trusted Computing. Fraunhofer SIT's involvement ranges from the standardization body over practical implementations to fundamental research. Fraunhofer SIT is involved throughout all application sectors, from desktop and server equipment, over automotive and railway to industrial applications.
Fraunhofer SIT's offers include:
*application sector specific design and architectures for TPM-based security solutions
*consultancy, teaching and empowerment on TPM integration
*extension and customizations of the Open Source Software Stack

GlobalSign provides PKI-based device identity enrollment and management solutions that leverage Infineon products such as the OPTIGA™ TPM SLM 9670 and SLB 9670 as the trust anchor. GlobalSign´s security products are targeted towards various IIoT verticals, including but not limited to - smart manufacturing, automotive, industrial automation and healthcare. GlobalSign brings experience and expertise in using PKI and SSL technologies and applying them towards solving cybersecurity problems in various small and large business contexts through their comprehensive product portfolio.
GlobalSign IoT Identity Platform can create and host custom PKI hierarchies that serve the core identity needs of devices embedded with Infineon OPTIGA™ TPMs.
GlobalSign IoT Edge Enroll is an endpoint software application that can provide device registration, enrollment and provisioning services. More information

Sectigo provides a complete certificate management solution starting with secure certificate creation & insertion at the customer´s factory using the OPTIGA™ TPM for private key storage. The Floodgate Factory CA Server enables key management and certificate signing during manufacturing. The Floodgate TPM Library provides the device-side software to streamline TPM usage and key storage, while the Floodgate CA Server allows management of PKI certificates after the device is deployed.Floodgate TPM Library and the Floodgate PKI Client enable OEMs to develop and deploy secure embedded connected devices with relative ease.
Together, Sectigo and Infineon provide:
- the APIs, libraries, and code running on the device to enable integration with the OPTIGA™ TPM
- key generation by the OPTIGA™ TPM and enrollment with Certificate Authority
- Certificate Signing Requests using the Simple Certificate Enrollment Protocol (SCEP), Enrollment over Secure Transport (EST), and Online Certificate Status Protocol (OCSP)
- Full integration with public and private Certificate Authorities

With about 15 years of experience in different security related projects and applications, Mixed Mode is a knowledgeable Infineon partner offering consulting services and software development for integration of the OPTIGA™ TPM. Amongst different projects, Mixed Mode developed and implemented a secure boot and secure update concept including hardware integration as well as verification of the LINUX image.
Mixed Mode has experience on different target embedded platforms, operating systems and use cases secured by OPTIGA™ TPM:
- Supported platforms: LINUX, RTOS, Bare Metal
- Supported use cases: Secure Communication, Secure Storage, Secure Boot, Secure Update
- Consulting services: Training, Workshops, Security Concepts / Security by Design, Code and Gap Analysis, ISO 62443 SL 3, Policy and Certificate Concepts
- Others: DRM (Digital Rights Management) and License Management on Embedded Platforms

wolfTPM is a TPM 2.0 project, designed for embedded use. It is highly portable, due to having been written in native C, having a single IO callback for SPI hardware interface, no external dependencies, and its compacted code with low resource usage.
It is generally very easy to compile on new platforms, so if your desired platform is not listed as supported or you would like assistance porting wolfTPM, please contact wolfSSL at facts@wolfssl.com.
Features:
*Provides all TPM 2.0 API's in compliance with the specification.
*Uses the TPM Interface Specification (TIS) to communicate over SPI.
*Includes wrappers for Key Generation, RSA encrypt/decrypt, ECC sign/verify, ECDH, NV Access and Hashing.




